Secure Data Destruction Guide: A Mission-Driven Approach for Atlanta Businesses

Staring at a pile of old hard drives? It’s easy to see them as just clutter, but you should think of them as unlocked filing cabinets sitting on the curb, packed with years of sensitive company, employee, and customer information. Secure data destruction is the only process that truly locks those cabinets and ensures the information inside is permanently and irretrievably gone, protecting your organization from what could be a catastrophic breach.
Why Data Destruction Is Your First Line of Defense
Improperly discarded IT equipment is a massive, often overlooked, liability. It’s a common misconception that hitting 'delete' or formatting a hard drive wipes the slate clean. That's dangerously incorrect.
These simple actions just remove the pointers to your files, leaving the actual data perfectly intact and surprisingly easy to get back with basic, widely available software tools.
This leftover information is known as data remanence, or sometimes "ghost data." It's the digital equivalent of tossing a sensitive client contract into the trash without shredding it first. Anyone who happens upon that discarded drive can potentially access everything from financial records and trade secrets to protected health information (PHI).
The Real Risks of Inaction
Overlooking secure data destruction isn't a minor slip-up; the consequences can be severe. A single forgotten server in a storage closet or a box of old company laptops could be the source of a major data breach. The fallout often includes significant financial penalties, messy legal battles, and irreversible damage to your brand’s hard-won reputation.
For industries like healthcare and finance, the stakes are even higher. Non-compliance with regulations such as HIPAA and GLBA can trigger multi-million-dollar fines.
Secure data destruction is not just an IT cleanup task; it's a critical business strategy for risk management. Failing to implement a secure process is like leaving your company’s digital front door wide open.
This is especially true for regulated sectors. Secure data destruction is a non-negotiable part of implementing top healthcare data security solutions and is absolutely essential for ensuring patient safety and regulatory adherence.
A Proactive Approach to Security
A proactive approach to data destruction turns this gaping liability into a secure, closed loop. This guide is meant to be a clear, actionable roadmap for any IT manager or compliance officer in Atlanta. We'll walk through the different methods of data sanitization, help you navigate complex compliance requirements, and show you exactly what to look for when choosing the right partner.
For a deeper dive into the technical side of wiping data, you can learn more about what data sanitization involves.
By the time you're done, you'll see how secure disposal doesn't just protect your organization—it can be part of a greater social mission. Choosing a partner like Atlanta Green Recycling allows your business to meet the most stringent security needs while making a real impact by supporting veterans and environmental restoration. Your old tech can do more than just disappear; it can help restore lives and landscapes.
Understanding Your Data Destruction Options
Once you realize that simply hitting "delete" isn't enough, the next step is figuring out how to properly destroy your data. It sounds technical, but it’s actually pretty straightforward when you break it down. The right method for you will hinge on your security policies, the kind of media you’re getting rid of, and any compliance rules you have to follow.
Let’s cut through the jargon and look at the three main techniques.
Data Wiping: The Clean Slate
First up is data wiping, which you might also hear called data sanitization. Think of your hard drive like a whiteboard. When you delete a file, you’re just erasing a small corner—the old writing is gone, but a faint impression is often left behind. Formatting the drive is like giving it a quick wipe with a dry cloth; it looks clean, but a determined person could still make out the original message.
Secure data wiping, on the other hand, is like scrubbing the entire board clean with a special solution until there's absolutely no trace of what was there before. Specialized software overwrites every single bit of the drive with random data, often multiple times, following strict protocols like the Department of Defense (DoD 5220.22-M) standard.
The big win here? The hardware is perfectly fine afterward. This means drives can be safely reused, resold, or donated, which is great for your budget and the planet.
Degaussing: The Magnetic Scramble
Next, we have degaussing. If you remember old cassette tapes, imagine holding a powerful magnet right up to one. That magnet would instantly scramble the magnetic particles on the tape, turning your favorite songs into silent static. Degaussing does the same thing to traditional hard disk drives (HDDs).
It uses a super-strong magnetic field to completely neutralize the magnetic storage on a drive's platters, making the data instantly and permanently unreadable. It's incredibly fast and effective for older, magnetic-based media. The catch? It’s totally useless on modern Solid-State Drives (SSDs), since they store data electronically, not magnetically.
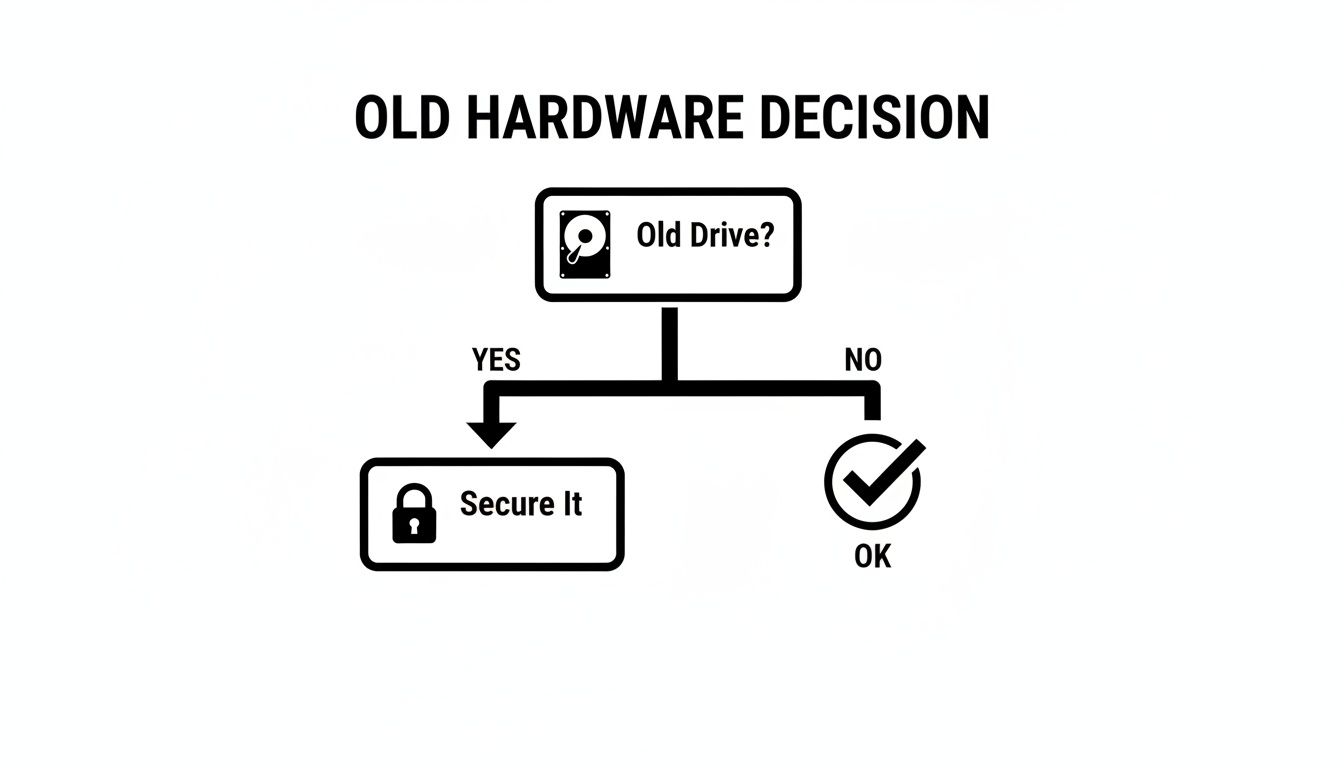
This simple decision tree shows the first question every organization needs to ask when retiring old hardware.
It’s a basic but critical reminder: every old drive is a potential security liability until it’s been properly sanitized.
Physical Destruction: The Final Word
Finally, we have physical destruction—the most surefire method of all. This is the digital equivalent of putting a sensitive document through a cross-cut shredder. Once it's turned into a pile of confetti, there’s no piecing it back together.
Physical destruction is the only method that gives you absolute, visual proof that the media is destroyed and the data is gone for good.
This is the gold standard for devices with top-secret information or for any media that’s broken or can’t be wiped, like many SSDs. Industrial-grade shredders grind hard drives, tapes, and SSDs into tiny, mangled pieces of metal and plastic, making data recovery impossible.
Comparing Secure Data Destruction Methods
To make the choice clearer, let's put these methods side-by-side. Each has its place, and understanding the differences is key to building a smart IT asset disposition plan.
| Method | How It Works | Best For | Key Advantage | Key Disadvantage |
|---|---|---|---|---|
| Data Wiping | Software overwrites all data on the drive with random characters, often in multiple passes. | Functional hard drives and SSDs intended for reuse, resale, or donation. | Hardware Preservation: The drive remains fully functional and can be redeployed. | Time-consuming for large numbers of drives; may not work on damaged media. |
| Degaussing | A powerful magnetic field instantly neutralizes the magnetic storage on a drive's platters. | Functional HDDs and magnetic tapes requiring rapid, high-volume sanitization. | Speed and Efficiency: Instantly renders data on magnetic media unrecoverable. | Ineffective on SSDs: Does not work on non-magnetic media and renders HDDs unusable. |
| Physical Destruction | Industrial shredders or crushers grind, bend, and break the media into small fragments. | All media types, especially SSDs, damaged drives, and devices with highly sensitive data. | Ultimate Security: Provides visual confirmation that data is 100% irretrievable. | No Reuse: The hardware is completely destroyed and cannot be repurposed. |
Ultimately, choosing the right method is a critical security decision. For businesses in our area looking for the highest level of assurance, a certified partner can provide expert guidance on professional hard drive destruction services to guarantee compliance and peace of mind.
Navigating the Complex World of Compliance
Picking a data destruction method is only half the battle. The real challenge? Making sure that method satisfies a tangled web of legal requirements.
For organizations in Atlanta and beyond, compliance isn't just about ticking boxes on a checklist—it's about actively dodging catastrophic fines, legal battles, and the kind of reputational damage that can haunt a company for years. Think of these regulations as the "why" behind every secure data destruction policy you create.
This is especially true for businesses in tightly regulated industries. For a hospital, a single hard drive tossed in a dumpster with patient records could easily trigger a multi-million-dollar HIPAA violation. In the same vein, a financial firm that fails to properly destroy old loan documents on retired servers could find itself facing serious penalties under the Gramm-Leach-Bliley Act (GLBA). These laws aren't just suggestions; they have very real teeth.
The Major Regulations Driving Data Destruction
While there are countless laws governing data privacy, a few key pieces of federal legislation really set the standard for most industries. Getting a handle on their core requirements is the first step toward building a data destruction program that can actually stand up to scrutiny.
- HIPAA (Health Insurance Portability and Accountability Act): This is the big one for patient privacy. HIPAA requires healthcare providers and their partners to have solid safeguards in place to protect sensitive patient health information (PHI). This includes very specific rules for the "final disposition" of PHI, making secure data destruction a non-negotiable part of the IT asset lifecycle.
- GLBA (Gramm-Leach-Bliley Act): This impacts nearly every financial institution, from local banks to massive investment firms. GLBA insists that companies protect consumers' private financial information. A key part of this is the Safeguards Rule, which mandates a written information security plan that must include the secure disposal of customer data.
- FACTA (Fair and Accurate Credit Transactions Act): This act was put in place to protect consumers from the nightmare of identity theft. The FACTA Disposal Rule requires businesses to take "reasonable measures" to destroy consumer report information, ensuring it's completely unreadable and can't be pieced back together.
The growing focus on these rules is obvious when you look at the market. The global secure data destruction industry has jumped from $3.35 billion to $3.7 billion in just one year. That explosion is being directly fueled by strict laws that demand the secure disposal of sensitive data to protect people and help companies avoid huge legal headaches.
The Audit Trail: Your Last Line of Defense
Here’s a hard truth: proving you followed the rules is just as important as the destruction itself. If an auditor comes knocking or you're facing a data breach investigation, they won't just take your word for it. They'll demand proof. This is where your audit trail becomes your most valuable asset.
An audit trail is simply the documented, unbroken history of your IT assets, from the second they leave your facility to their final destruction. This chain of custody has to be logged with painstaking detail, tracking things like serial numbers and getting confirmation at every single step.
The single most important document in your audit trail is the Certificate of Destruction. This legally binding document serves as your official receipt, proving that your data was destroyed in a compliant, secure, and permanent manner.
Without that certificate, you have no verifiable proof of compliance. It's that simple. That's why partnering with a certified vendor who provides this documentation is absolutely critical. To manage these complex rules and stay ahead of data leaks, many companies use modern compliance risk management software to keep their processes tight.
Ultimately, choosing a partner who lives and breathes these complex requirements is the best way to get some peace of mind. For a closer look at the practical steps involved, check out our guide on how to completely wipe a hard drive.
How to Choose the Right Data Destruction Partner
Picking a vendor for secure data destruction is so much more than a simple logistical decision—it’s a critical choice for your company's security and compliance. Your partner becomes an extension of your security team, and the wrong one can expose you to unimaginable risk. For any Atlanta-based organization, this is a methodical process that has to focus on certifications, ironclad security, and a completely unbroken chain of custody.
This decision is just too important to leave to chance. A partner's failure can easily become your organization’s next data breach, making a thorough evaluation absolutely non-negotiable.
The Vendor Vetting Checklist
When you're evaluating potential partners, your questions need to be direct and demanding. Any hesitation to give you straight answers on their security protocols is a massive red flag. Use this checklist as a starting point for your own due diligence.
-
Industry Certifications: Ask them point-blank: Are you NAID AAA or R2 certified? These aren’t just logos for a website; they are concrete proof that a vendor sticks to the highest industry standards for secure data destruction and responsible electronics recycling. Getting certified requires them to pass tough, unannounced audits from third parties.
-
Chain of Custody: Have them walk you through their entire chain-of-custody process, step by step. It should be a completely closed-loop system, with detailed tracking from the second an asset leaves your building until you have a Certificate of Destruction in your hands. This means locked transport, secure facilities, and serialized asset tracking.
-
Security Protocols: What are their facility's security measures? You should be looking for 24/7 monitored surveillance, restricted access control, and rigorous employee background checks. These protocols are what ensure your assets are protected at every single stage.
-
Service Flexibility: Do they offer both onsite and offsite services? A quality vendor can accommodate your specific security needs, whether that means bringing a mobile shredding truck to your parking lot or providing secure transport to their facility. For businesses needing the highest level of assurance, exploring options for onsite hard drive shredding is often a must-have.
Beyond Security: Aligning with Corporate Values
In today’s world, compliance is just the baseline—it’s not the end goal. A true partnership goes beyond the technical details to align with your organization’s bigger mission. Choosing a vendor isn't just about what they do; it's about what they stand for.
This is where a mission-driven partner can turn a routine compliance task into a powerful story about your company's values. By picking a vendor that weaves social and environmental impact into its core operations, you can meet your security needs while also hitting your Environmental, Social, and Governance (ESG) and Corporate Social Responsibility (CSR) goals.
"Your old tech can house a veteran and grow a forest." This isn't just a tagline; it's a whole new way of looking at IT asset disposition. It transforms e-waste from a liability into an asset for community and environmental restoration.
Imagine turning your annual IT refresh into a tangible contribution that supports veterans and helps reforest our landscapes. This approach changes the whole conversation from a simple cost center to a value-added initiative.
Turning Compliance into a Powerful ESG Story
A purpose-driven secure data destruction partner gives you more than just a Certificate of Destruction. They deliver a story of impact that you can proudly share with your stakeholders, employees, and customers.
Think about a partnership that provides:
- Veteran Support Impact Reports: Detailed documents showing how your recycled electronics have directly contributed to veteran aid programs.
- Plant-A-Tree Certificates: Official certificates for your CSR files, quantifying the number of trees planted because of your e-waste.
- "Recycled with Purpose" Eco-Badge: A digital badge for your website and sustainability reports, signaling your commitment to responsible and impactful recycling.
When you choose a partner like Atlanta Green Recycling, you’re not just ensuring secure data destruction. You are making a conscious choice to invest in a dual-impact model that restores both lives and landscapes. This allows your organization to confidently meet its security and compliance duties while championing a cause that resonates with your community and strengthens your brand.
The True Cost of a Data Breach
It’s easy to look at secure data destruction as just another line item on a budget—a necessary expense. That view is a dangerous miscalculation. A much smarter way to see it is as a critical form of risk management. It's an investment that directly shields your organization's finances and reputation from a potential catastrophe. Choosing to do nothing, on the other hand, comes with a price tag that can be absolutely devastating.
Data breaches aren't some far-off threat anymore; they're a common and incredibly expensive part of doing business. In just one recent year, breaches hit over 353 million people, with the fallout shaking organizations to their core. The average cost of a single data breach globally has now hit a jaw-dropping $4.45 million, a number that can easily cripple a successful company.
For businesses here in the United States, the picture is even grimmer, averaging $5.09 million per incident. And when you add ransomware attacks into the mix—which often get in through security holes on old, improperly handled hardware—that cost jumps by another $1.85 million.
A Story of Preventable Disaster
To really grasp the stakes, let’s imagine a scenario that is all too plausible for a local Atlanta clinic. They're consolidating offices, and in the shuffle, a single old server is left behind in a storage closet. A few months later, it’s mistakenly sent to a general scrap yard instead of a certified data destruction partner.
That one server holds the unencrypted health records of thousands of patients.
Before long, that server’s hard drives are sold online. Someone with basic data recovery tools gets their hands on it and accesses the entire patient database. The clinic is suddenly staring down the barrel of a massive HIPAA investigation, with fines that can soar to $50,000 per violation. Patients file class-action lawsuits, the local news picks up the story, and the clinic's hard-won reputation is destroyed.
This entire multi-million-dollar disaster wasn't the work of a sophisticated team of international hackers. It was caused by one forgotten server and a broken disposal process.
Shifting from Expense to Investment
This story drives home a vital point: the cost of professional, certified data destruction is a tiny fraction of what a single breach can cost you. Proper disposal isn't just about getting rid of old gear; it's about slamming the door on a major security vulnerability that far too many organizations leave wide open. To see how this fits into a bigger strategy, check out our guide on IT asset management best practices.
When you invest in a certified process, you're buying peace of mind. You're getting a guarantee that every single device, whether it's one laptop or a data center full of servers, is handled with an ironclad chain of custody. You're ensuring that the data on them is made completely and forever unrecoverable. This simple step turns a huge potential liability into a secure, verifiable, and auditable final chapter for your IT assets, protecting both your bottom line and the trust you've built with your customers.
Turning E-Waste Into a Force for Good
After navigating the technical requirements and compliance mandates of secure data destruction, there's a final, powerful question to consider: What if your retired IT assets could do more than just disappear securely?
What if they could become a restorative force for both people and the planet? This is where a routine compliance task transforms into a meaningful mission.
At its core, secure data destruction is all about mitigating risk. The staggering growth of cybercrime—predicted to cost the world $10.5 trillion USD annually—paints a clear picture of the threat landscape. Improperly disposed IT equipment is a prime target, acting as a potential entry point for attacks.
For Atlanta businesses, this makes professional data destruction not just a best practice but a financial imperative that is far more cost-effective than a breach. You can get more insights on this growing threat on Cybersecurity Ventures.
Choosing the right partner allows you to address this risk while simultaneously creating positive change.
From E-Waste to ESG Wins
Atlanta businesses are increasingly focused on their Environmental, Social, and Governance (ESG) and Corporate Social Responsibility (CSR) goals. A mission-driven data destruction partner provides a direct and simple way to advance these objectives.
Instead of being a sunk cost, your e-waste becomes a tangible contribution to vital causes.
This is the heart of our dual-impact model at Atlanta Green Recycling. We connect every piece of recycled technology to two critical missions: supporting U.S. veterans and reforesting our nation's landscapes.
"Your old tech can house a veteran and grow a forest." This simple statement captures a powerful truth—your decommissioned assets have the potential to restore lives and landscapes, turning a security requirement into a story of hope.
This approach reframes the entire process. A corporate IT refresh is no longer just about new equipment; it's an opportunity to plant a new grove of trees. Decommissioning a data center becomes a way to provide essential aid to veterans in our community.
Making Your Impact Tangible
A genuine commitment to corporate responsibility requires more than just good intentions; it demands transparency and measurable results. That’s why we provide our partners with the tools they need to document and celebrate their contributions.
This transforms your secure data destruction process into a powerful asset for your brand and your sustainability reporting. We offer:
- Veteran Support Impact Reports: These documents detail how your organization’s e-waste has directly funded aid programs for veterans.
- Plant-A-Tree Certificates: For every qualifying pickup, you receive official certification documenting the number of trees planted in your company’s name.
- "Recycled with Purpose" Eco-Badge: A digital badge that partners can display on their websites and in CSR reports, showcasing their commitment to a circular economy with a cause.
By choosing a partner that is not only secure and compliant but also meaningful and restorative, you make a powerful statement. You demonstrate that your organization’s commitment to security is matched by its dedication to community and environmental stewardship.
It’s a choice to turn e-waste into hope, ensuring that the end of your technology’s lifecycle marks the beginning of something better.
Frequently Asked Questions About Data Destruction
Even when you have a solid plan in place, specific questions always pop up during a data destruction project. We get it. Here are the answers to some of the most common things we hear from Atlanta businesses, designed to give you the confidence to move forward.
Is Physically Destroying a Hard Drive Better Than Wiping It?
This really comes down to what you plan to do with the asset next. Wiping, which is also called data sanitization, is perfect if you want to reuse or resell the equipment. It completely erases every bit of data but leaves the hard drive itself perfectly functional, which is a great move for your budget and the environment.
On the other hand, physical destruction is the final word in data security. Shredding a drive makes it impossible to operate and renders the data completely unrecoverable. For devices that held your most sensitive information, or for any media at the true end of its life, shredding is often the only way to satisfy strict compliance rules.
What Is a Certificate of Destruction and Why Do I Need One?
Think of a Certificate of Destruction as your official receipt for proper data disposal. It’s a formal document that serves as an audit trail, giving you concrete proof that your data-bearing assets were destroyed securely and according to regulations.
This certificate is your number one defense if an auditor or lawyer comes knocking. It typically lists device serial numbers, the exact method of destruction used, and the date of service. For regulations like HIPAA and FACTA, it's not just a nice-to-have; it's a critical piece of documentation that shields your organization from serious liability.
Does Formatting a Hard Drive Count As Secure Data Destruction?
Absolutely not. It's a common misconception, but formatting a drive is nowhere near secure. All it does is remove the file system's "pointers" that tell the computer where the data is. The actual information is still there, and it can be recovered with surprising ease using basic software tools.
True secure data destruction means you either have to overwrite the data multiple times with specialized software or physically obliterate the media. Anything less leaves you exposed.
How Do You Handle Data Destruction for Solid-State Drives (SSDs)?
Solid-State Drives (SSDs) are a different beast from traditional magnetic hard drives (HDDs), and they need to be handled differently. Their data storage method makes some old techniques useless. While specialized software can wipe an SSD, the most surefire method is always physical shredding.
It's crucial to know that degaussing—a process that uses powerful magnets to erase data—is completely ineffective on SSDs. They don't store data magnetically. A certified partner will use industrial shredders built to grind SSDs into tiny particles, ensuring no data can ever be pulled from the memory chips.
At Atlanta Green Recycling, we do more than just provide secure, certified data destruction. Our tagline says it all: "Recycling That Restores Lives and Landscapes." We help Atlanta businesses meet their ESG goals by supporting U.S. veterans and planting trees with every single pickup. Partner with us to transform your retired IT assets into a powerful story of community support. Learn more and schedule your secure recycling pickup at https://www.greenatlanta.com.