A Guide to Secure Hard Drive Disposal in Atlanta

When you’re talking about secure hard drive disposal, it’s about a lot more than just dragging files to the trash can. Real data security means using methods like software wiping, degaussing, or even physical shredding to make sure that data is gone for good—completely unrecoverable. For any Atlanta business, this isn't just a simple IT task. It’s a core security protocol that protects your most sensitive information and keeps you on the right side of the law.
Why Secure Hard Drive Disposal Is a Business Imperative
In today's business world, data is currency. So, treating your old hard drives like any other piece of office junk is a massive misstep. That outdated tech isn't just taking up space in a supply closet; it’s a ticking time bomb of security risks, holding onto confidential information long after a device has been retired. Getting rid of it the right way isn't about tidying up—it’s a fundamental part of a smart corporate governance strategy.
This whole process is more than an IT function; it's a strategic decision with real financial, legal, and reputational consequences. If you fail to properly destroy the data on old computers, servers, or external drives, you're turning that discarded equipment into a direct liability.
Protecting Your Bottom Line and Reputation
The financial hit from a data breach can be absolutely staggering, and it goes way beyond the immediate cleanup costs. You’re looking at potential fines from regulatory bodies, expensive legal battles from lawsuits, and the kind of long-term damage to customer trust that can cripple a company.
Regulatory compliance is a huge driver here. Laws like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) have incredibly strict rules for destroying sensitive data. Getting it wrong can lead to serious penalties—GDPR fines can go as high as 4% of annual global turnover or €20 million.
A single mishandled hard drive can destroy years of brand-building and customer loyalty. When customers give you their data, they expect that trust to cover the entire data lifecycle, especially its secure end-of-life.
A properly managed disposal process protects you from these threats. The table below breaks down just how different the outcomes can be.
Risks of Improper Disposal vs Rewards of Secure Disposal
| Risk Area | Consequences of Improper Disposal | Benefits of Secure & Ethical Disposal |
|---|---|---|
| Financial | Hefty fines, legal fees, breach remediation costs, and lost revenue. | Avoidance of penalties, reduced legal risk, and potential cost savings from asset remarketing. |
| Reputation | Irreparable brand damage, loss of customer trust, and negative press. | Enhanced brand image as a responsible and trustworthy company. |
| Legal & Compliance | Non-compliance with HIPAA, GDPR, FACTA, and other regulations. | Guaranteed compliance with all relevant data protection laws. |
| Data Security | High risk of data breaches, intellectual property theft, and corporate espionage. | Complete elimination of data breach risks from end-of-life assets. |
| Environmental | Fines for improper e-waste disposal and negative environmental impact. | Positive CSR and ESG reporting, demonstrating a commitment to sustainability. |
As you can see, the choice is pretty clear. Proactive, secure disposal isn't a cost center—it's an investment in your company's stability and future.
Turning Compliance Into a Competitive Advantage
While the risks are very real, a smart approach to secure hard drive disposal can open up incredible opportunities. It lets your company build a powerful story around corporate social responsibility (CSR) and environmental, social, and governance (ESG) principles. Suddenly, a necessary security task becomes a narrative that connects with today’s consumers and stakeholders, positioning your company as an easy ESG win.
Think about it: what if your disposal process did more than just protect data? Imagine a model where your company’s retired IT assets become a force for good. By teaming up with a mission-driven organization, you can make sure your old tech is disposed of in a way that gives back to the community.
For companies here in Atlanta, that means your old equipment can directly help local causes. This is where a dual-impact model really shines:
- Veteran Support: A portion of the value from your recycled materials can go toward funding programs that provide housing and aid to veterans.
- Environmental Stewardship: Your e-waste can sponsor tree-planting efforts, helping with reforestation and contributing to a healthier planet.
This strategy turns a routine compliance task into a genuine brand asset. A message like, “Your old tech can house a veteran and grow a forest,” connects an internal process to an emotional, tangible result. This isn't just recycling; it's recycling with a purpose, showing a commitment that goes beyond the bottom line. When you highlight these efforts in your CSR reports, you create a clear competitive advantage. To learn more about the broader environmental context, check out our guide on the benefits of e-waste recycling.
Choosing the Right Data Destruction Method
Once you've mapped out your disposal strategy, the real work begins: picking the right way to destroy the data on your hard drives. This isn't a one-size-fits-all decision. The best method depends entirely on your security posture, compliance mandates, and whether you plan to squeeze a little more life out of the hardware itself.
Making the right call here is the difference between simply getting rid of old gear and executing a certified, auditable data destruction process.
There are three industry-standard ways to tackle this: software wiping, degaussing, and good old-fashioned physical shredding. Each one lines up with different security levels defined by the National Institute of Standards and Technology (NIST), which sets the gold standard for what data sanitization entails in our detailed guide.
The NIST SP 800-88 Standard: Your Compliance Roadmap
When we talk about data destruction, everything comes back to NIST Special Publication 800-88. It’s the playbook, and it breaks down media sanitization into three distinct actions: Clear, Purge, and Destroy. Think of them as escalating levels of security, each designed for a specific job.
- Clear: This is about using software to overwrite data in all the spots a user can normally access. It's a solid defense against basic, non-invasive recovery attempts.
- Purge: This level steps things up. It uses physical or logical methods to make data recovery impossible, even with state-of-the-art lab equipment.
- Destroy: This is the final word in data destruction. The media is rendered totally unusable, and there’s zero chance of recovering anything.
The guidelines from NIST are pretty clear about what works for what.
As you can see from the NIST table, there's no single magic bullet—the right tool depends on the type of storage media you're dealing with.
Software Wiping: Giving Your Assets a Second Life (NIST Clear)
Software-based wiping is exactly what it sounds like. Specialized programs overwrite every bit of existing data on a hard drive with random characters, usually in several passes. This process effectively buries the original information, making it incredibly difficult to get back using standard software tools.
The biggest upside? The hard drive is still perfectly functional. This makes it the go-to choice for companies looking to resell, donate, or redeploy older equipment.
Picture a small Atlanta-based marketing firm upgrading its workstations. They can use software wiping to securely erase the old drives before donating them to a local school. It’s practical, secure, and responsible. However, if you’re dealing with highly sensitive data or need to meet strict HIPAA rules, wiping alone might not be enough.
Degaussing: The Magnetic Wipeout (NIST Purge)
Degaussing is a show of force. It involves hitting a hard drive with a massive magnetic field that completely randomizes the magnetic particles on the platters where your data lives. It's an instant, permanent erasure that also renders the drive totally inoperable.
This technique is a beast when it comes to traditional magnetic hard disk drives (HDDs) and old-school magnetic tapes. But here's the catch: it does absolutely nothing to Solid-State Drives (SSDs), which don’t store data magnetically. A financial firm retiring a data center full of legacy servers with HDDs would find degaussing a brutally efficient way to meet the NIST Purge standard.
Physical Shredding: The Point of No Return (NIST Destroy)
When you need absolute, undeniable certainty that your data is gone forever, you shred it. An industrial-grade shredder literally grinds hard drives into a pile of tiny, mangled metal fragments. There's no putting Humpty Dumpty back together again.
Physical shredding is the only method that provides 100% certainty. For a healthcare provider protecting patient records under HIPAA or a government contractor handling classified files, shredding isn't just the best option—it's often the only compliant one.
This method leaves no room for doubt and guarantees you’re in line with the toughest data protection laws out there. It provides a definitive end to the data lifecycle, all backed up by a formal Certificate of Destruction.
Comparing Data Destruction Methods for Compliance
So, how do you choose? It really comes down to weighing compliance needs against your asset reuse goals. This table gives you a quick side-by-side look to help you decide what's right for your organization.
Comparing Data Destruction Methods for Compliance
| Method | NIST 800-88 Level | Best For | Allows Reuse? | HIPAA/GDPR Compliant? |
|---|---|---|---|---|
| Software Wiping | Clear | Securely reusing or donating hardware with low to medium sensitivity data. | Yes | Yes, in many cases, but requires careful validation. |
| Degaussing | Purge | Rapidly destroying data on a large volume of magnetic HDDs and tapes. | No | Yes, for magnetic media only. |
| Physical Shredding | Destroy | Eliminating highly sensitive data and ensuring maximum compliance for all drive types. | No | Yes, considered the most secure and definitive method. |
By carefully matching the method to your data's sensitivity and your regulatory obligations, you build a rock-solid defense against data breaches from your retired assets.
Implementing a Bulletproof Chain of Custody Process
The moment a hard drive leaves your direct control, a potential security gap opens up. True secure hard drive disposal isn't just about the final act of destruction; it's about maintaining an unbroken, documented trail from the moment an asset is retired to its final recycling.
This documented journey, known as the chain of custody, is your ultimate proof of compliance and due diligence. Without it, you're essentially just hoping for the best once your assets are out the door. A solid chain of custody turns that hope into certainty with an auditable record that shuts down risk and verifies every step.
The First Link: Asset Inventory and Secure Collection
The process kicks off the second a device is decommissioned. Your immediate task is to build a detailed inventory log. This isn't just about counting heads; each asset needs to be meticulously documented.
- Serial Numbers: Grab the unique serial number of every single hard drive or device.
- Asset Tags: Note any internal company asset tags you use for cross-referencing.
- Device Type: Be specific. Is it a laptop, a server HDD, or an external drive?
- Location: Document its last known department or location within your organization.
This initial log is the bedrock of your entire audit trail. Once documented, move the assets into a secure, locked container while they await pickup. This simple step prevents unauthorized access or assets mysteriously "walking away" before the handover even happens.
Secure Transportation: Documented Handoffs
The physical transport of your assets is often the most vulnerable point in the process. Any reputable vendor won't just show up with an open truck. Secure transit protocols are non-negotiable and must include locked vehicles, screened personnel, and a formal, documented transfer of custody. Thinking about physical security can even draw lessons from other industries that use robust theft prevention strategies to protect valuable assets in transit.
Every handoff is a critical control point. A formal signature, a timestamp, and a verification against the initial inventory log must happen every single time the assets change hands. This applies from your IT manager to the transport driver, and from the driver to the destruction facility staff.
This creates a seamless, accountable record. If there's any discrepancy between the initial log and what's received at the facility, it can be flagged and investigated immediately, closing a common loophole in the data security chain.
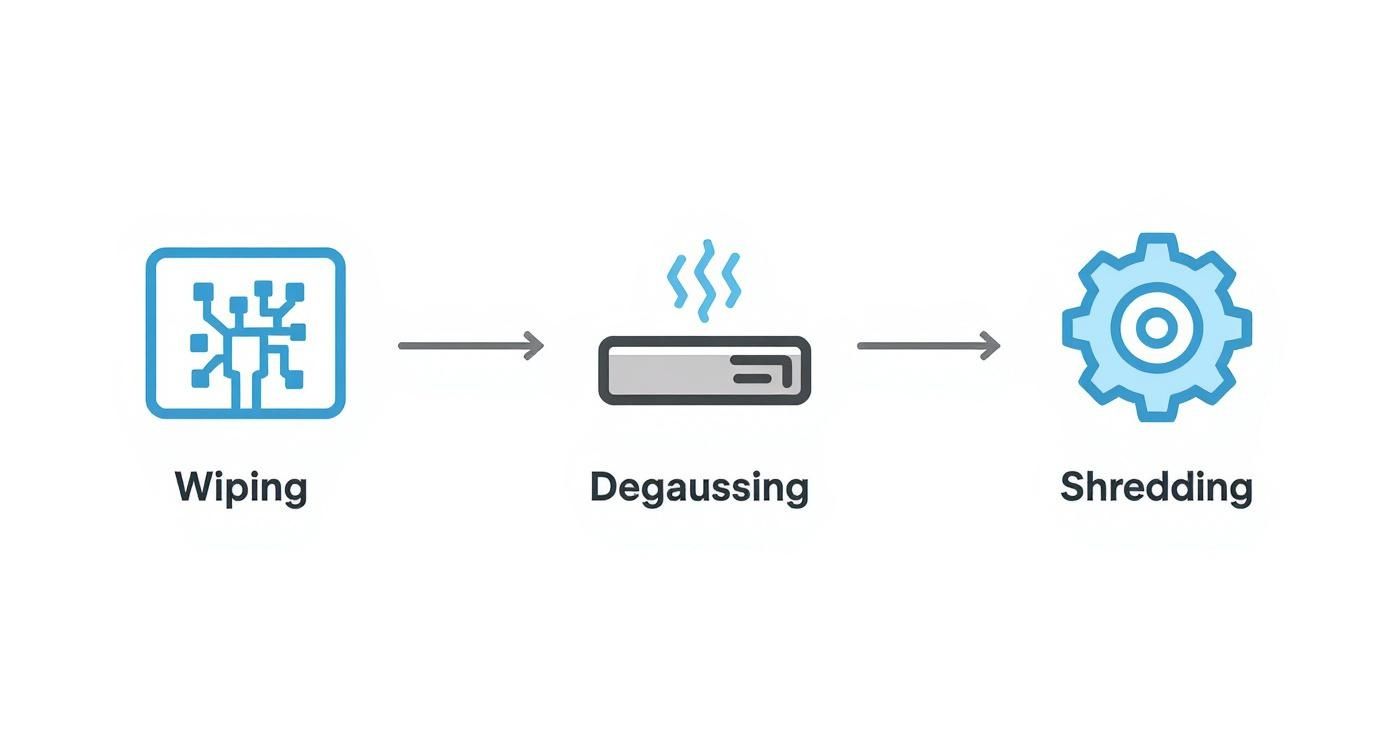
The infographic below shows the key destruction stages that happen at the end of this secure journey.
This flow highlights the final, irreversible steps—Wiping, Degaussing, and Shredding—that guarantee your data is completely unrecoverable.
Final Verification: The Certificate of Destruction
The chain of custody concludes with the single most important document you'll receive: the Certificate of Destruction (CoD). This isn't just a simple receipt. It's a legally binding affidavit confirming your assets were permanently destroyed.
A legitimate CoD is much more than a generic piece of paper. It should be serialized and packed with specific details that tie directly back to your initial inventory log.
Essential Elements of a Compliant CoD:
- A unique serial number for that specific destruction job.
- The date and method of destruction, clearly stating when and how the drives were destroyed (e.g., shredded, degaussed).
- An itemized asset list that includes the serial numbers of every device destroyed, matching your original inventory.
- Authorized signatures from a representative of the destruction facility.
- A statement of compliance, declaring the work was done according to relevant standards.
This final document closes the loop, giving you the irrefutable evidence needed for audits and compliance with regulations like HIPAA or GDPR. If you want to dig deeper into why this professional documentation is so critical, you can explore the key reasons to use a professional data destruction service in Atlanta.
Without a detailed CoD, your chain of custody is incomplete, leaving your organization exposed to serious liability.
How to Select a Secure Disposal Partner in Atlanta
Choosing the right partner for secure hard drive disposal is easily the most important decision in your entire end-of-life asset strategy. You aren't just hiring a vendor; you're entrusting a third party with your company's most sensitive data. In a market where trust is everything, your selection process has to be rigorous.
The demand for these services reflects just how high the stakes are. The hard drive destruction market was valued at around USD 1.5 billion in 2023 and is expected to more than double by 2032. This growth is pushed by strict data privacy laws and the sheer number of data-heavy industries right here in North America. For more context on these trends, you can discover key insights into the hard drive destruction service market.
This makes picking the right partner in Atlanta even more critical. You need a company that doesn't just check the boxes but actually elevates your security and CSR posture.
Look for Gold-Standard Certifications
Certifications are your first line of defense. They're independent proof that a company holds itself to the highest industry standards for both security and environmental responsibility. Never just take a vendor's word for it; ask to see the paperwork.
Two types of certifications are non-negotiable:
- NAID AAA Certification: This is the absolute gold standard for data destruction. It means the vendor has passed tough, unannounced audits on everything from employee screening and secure transport to their actual destruction processes. A NAID AAA certified partner guarantees a compliant, fully auditable chain of custody.
- R2 or e-Stewards Certification: These are all about environmental responsibility. They ensure your e-waste is recycled ethically, keeping hazardous materials out of landfills and making sure global best practices are followed.
A vendor without these certifications is a massive blind spot in your compliance strategy. They are the baseline proof that a company takes both data security and environmental stewardship seriously.
Asking a potential partner, "Are you NAID AAA certified?" should be one of your very first questions. It’s a simple yes-or-no qualifier that will save you from wasting time on providers who can't meet the most basic security benchmarks. For more guidance, our breakdown of top electronic waste disposal companies in Atlanta offers some great perspective.
Vet Their Audit and Documentation Process
A secure process is a documented one. Your partner absolutely must provide a detailed, unbroken audit trail from the moment your assets leave your building to their final destruction. This paperwork is your legal shield if a compliance audit ever comes knocking.
Insist on seeing samples of their key documents:
- Chain of Custody Forms: These should track every single handoff, complete with signatures, dates, and times.
- Serialized Asset Lists: The final report must match the inventory log you created, accounting for every device by its unique serial number. No exceptions.
- Certificate of Destruction (CoD): This is the final, crucial piece of paper. It should be a formal, serialized certificate that legally attests to the secure destruction of your specific assets.
A partner who gets vague or provides incomplete documentation isn't just unprofessional—they are a liability waiting to happen.
Go Beyond Compliance and Choose a Mission-Driven Partner
Once you've vetted the security and environmental credentials, the last piece of the puzzle is finding a partner whose mission clicks with your own company's values. This is where you can turn a necessary expense into a powerful ESG and CSR win for your brand.
Here in Atlanta, that means looking for a partner with deep local roots and a real commitment to community impact. A mission-driven provider can transform the act of recycling into a story you can proudly share with your stakeholders and customers. Imagine being able to report that your routine IT asset disposal also helped plant trees in local forests or provided direct aid to veterans in our community.
This dual-impact model turns a simple vendor choice into a strategic partnership. When you choose a recycler who can provide "Plant-A-Tree" certificates and "Veteran Support Impact Reports," you're not just disposing of hard drives—you're building a better brand and a stronger community. Ask potential partners, “How does your process help us meet our ESG goals?” Their answer will tell you everything you need to know.
Turning E-Waste Into a Positive Community Impact
You’ve done the hard work. You've figured out the best destruction methods, you’ve locked down your chain of custody, and you've followed all the steps for secure hard drive disposal. But what if the final step wasn't just about compliance? What if it was about making a real, tangible difference?
This is where the entire process shifts from being an operational headache to a powerful story for your brand. Instead of seeing old IT assets as a liability, you can start seeing them as a resource. With the right partner, that pile of retired hard drives can become a force for good.
The scale of this challenge is massive. Every year, between 20 and 70 million hard disk drives (HDDs) hit their end of life. These drives contribute to a global e-waste problem that tops 50 million metric tons per year. It's a staggering figure, and it's why major companies are now pushing for a 90% reuse and recycle rate for hard disks. You can see this in action by checking out Microsoft's initiative to save the planet one hard drive at a time.
The "Recycle for a Cause" Model
This is where things get interesting. A "Recycle for a Cause" approach connects the responsible act of recycling directly to measurable community benefits. It’s a model where the value recovered from your e-waste—after secure data destruction, of course—is funneled into verified philanthropic initiatives.
Suddenly, a standard operational procedure becomes a story of corporate responsibility that actually resonates with employees, customers, and stakeholders.
Your old tech can house a veteran and grow a forest. This isn't just a tagline; it's a tangible outcome. A mission-driven partner provides transparent reporting showing exactly how your company’s recycling efforts are making a difference.
Imagine your next corporate sustainability report featuring live impact counters, proudly displaying stats like "1,245 veterans supported" and "3,700 trees planted." That's the power of turning e-waste into hope.
How Corporate Recycling Drives Fuel Community Impact
This model works because it's built on simple, easy-to-implement partnerships for businesses like yours. A mission-focused recycling partner in Atlanta can offer services designed to make participation effortless while maximizing your company's positive influence.
Here's how it usually works:
- Corporate Recycling Drives: A partner offers free pickup for a set number of devices (say, 50+), handling all the logistics. This removes the operational friction for your team.
- Secure Destruction First: Every single data-bearing device undergoes certified data destruction. Your security and compliance are always the top priority.
- Value Recovery for Good: After destruction, the raw materials are responsibly recycled. A portion of the proceeds is then donated to vetted nonprofit partners.
- Documented Impact: You receive official documentation for your CSR records, like "Plant-A-Tree" certificates and "Veteran Support Impact Reports," proving your contribution.
This structured process is a clear win for your company's ESG goals. You meet your security obligations while generating positive social and environmental outcomes. This is especially vital for businesses that need comprehensive product destruction services that align with their brand values.
Building a Better Brand and a Better Atlanta
By choosing a secure disposal partner committed to local initiatives, you're not just recycling—you're investing right back into your own community. This creates a powerful local narrative you can share through press features, social media, and internal communications.
Try aligning your recycling drives with seasonal events like Veterans Day, Earth Day, or Arbor Day to amplify your message and get your employees engaged in something truly meaningful. Co-hosting recycling drives with VFW chapters or environmental NGOs can further strengthen this "Greener Atlanta" initiative.
This approach builds a legacy that extends far beyond data security. It shows that your company understands its role in the community and is actively working to restore lives and landscapes. The final step in secure hard drive disposal, then, isn't just a step—it's a choice to turn your e-waste from a problem into a promise for a better tomorrow.
Got Questions About Hard Drive Disposal? We Have Answers.
Even with a solid plan for secure hard drive disposal, questions inevitably pop up. Here are some straightforward answers to the most common queries we get from Atlanta businesses. Think of this as your quick reference guide for making smart, secure decisions.
Is It Okay to Just Smash a Hard Drive with a Hammer?
While taking a hammer to an old hard drive might feel satisfying, it’s a terrible idea from a security standpoint. It is not a compliant or secure disposal method, period.
You’d be surprised how resilient the magnetic platters inside a hard drive are. A determined data thief can often pull significant amounts of data from platters that are just cracked or bent. To truly meet the NIST 800-88 “Destroy” standard, you need professional shredding that turns drives into tiny, unrecoverable fragments. Besides, the hammer method does nothing to address the hazardous electronic components inside the drive that need responsible recycling.
What Is a Certificate of Destruction and Why Do I Need One?
A Certificate of Destruction (CoD) is your official, legal proof that specific data-bearing assets have been permanently destroyed. It's an absolutely critical piece of your audit trail, especially for proving compliance with regulations like HIPAA or GDPR.
A proper CoD isn't just a receipt—it's an affidavit that formally transfers liability from your company to the destruction vendor. It’s your proof of due diligence if you ever face a security audit or legal challenge.
This document should be serialized and detail exactly what was destroyed, the date, and the method used. Most importantly, it must include an itemized list of serial numbers for every single device, creating an unbroken and auditable record from start to finish.
On-Site vs. Off-Site Shredding: Which Is Right for Me?
Certified vendors here in Atlanta will offer both on-site and off-site shredding. The best option really just boils down to your organization's specific security needs and comfort level.
- On-Site Shredding: A mobile destruction truck comes right to your facility. You get to physically watch your hard drives get shredded, which provides the ultimate peace of mind. This is the go-to choice for organizations with extremely sensitive data, like hospitals or financial firms.
- Off-Site Shredding: This process involves securely transporting your assets in locked containers via tracked vehicles to a specialized, monitored facility. A strict chain of custody is maintained from the moment the drives leave your building until they are destroyed.
Both methods are incredibly secure and follow a rigorous chain of custody, ensuring the integrity of the process no matter which you choose.
How Can Recycling My E-Waste Actually Support a Social Cause?
This is where things get really interesting. Modern recycling models can create a direct link between responsible e-waste disposal and doing some real good in the community. It turns what used to be a simple compliance chore into a powerful story of corporate citizenship.
Here’s how it works: after your data is certifiably destroyed, a portion of the revenue from recycling the raw materials in your old electronics is donated to verified nonprofit partners. These funds can directly support vital community programs. For example, your company’s retired IT gear can translate into tangible aid for local veterans or help fund tree-planting through reforestation initiatives. Your e-waste goes from being a liability to a measurable force for positive change.
Ready to turn your retired IT assets into a force for good? At Atlanta Green Recycling, we provide NAID AAA certified secure hard drive disposal that not only protects your data but also supports veterans and restores our local environment. Our “Recycling That Restores Lives and Landscapes” approach gives you peace of mind and a powerful story of community impact. Schedule your secure, mission-driven electronics recycling pickup today.
Schedule Your Secure E-Waste Pickup with Atlanta Green Recycling